PKI Configuration Example
This section describes an example of creating a security alliance by IKE. The authentication policy of IKE adopts PKI certificate system.
Networking Requirement
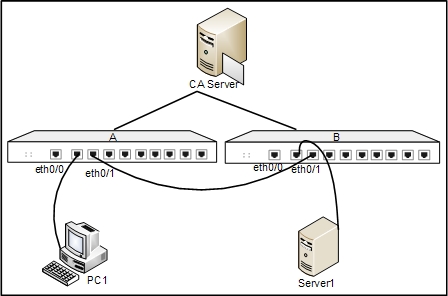
The goal is to create a secure tunnel between Device A and Device B. PC1 is used as the host of Device A, with the IP address being 10.1.1.1, and the gateway address is 10.1.1.2; Server1 is used as the server of Device B, whose IP address is 192.168.1.1, and the gateway address is 192.168.1.2. The requirement is: protecting the traffic between the subnet represented by PC1 (10.1.1.0/24) and the subnet represented by server1 (192.168.1.0/24). The authentication policy adopts PKI certificate system, using security protocol ESP and encryption algorithm 3DES, and the Hash algorithm is SHA1. The networking topology is shown as follows:
Configuration Procedure
Take the following steps:
Step 1: Configure interfaces.
Device A
- On the Navigation pane, click Configure > Network > Network to visit the Network page.
- Select ethernet0/0 from the interface list, and click Edit. In the Interface Configuration dialog, configure the options as below:
- Binding zone: Layer 3 zone
- Zone: trust
- Type: Static IP
- IP address: 10.1.1.2
- Netmask: 255.255.255.0
- Click OK to save your settings and return to the Network page.
- Select ethernet0/1 from the interface list, and click Edit. In the Interface Configuration dialog, configure the options as below:
- Binding zone: Layer 3 zone
- Zone: untrust
- Type: Static IP
- IP address: 1.1.1.1
- Netmask: 255.255.255.0
- Click OK to save the changes and return to the Network page.
- Click New, and select Tunnel Interface from the drop-down list. In the Interface Configuration dialog, configure the options as below:
- Name: tunnel1
- Binding zone: Layer 3 zone
- Zone: trust
- Click OK to save your settings and return to the Network page.
Device B
- On the Navigation pane, click Configure > Network > Network to visit the Network page.
- Select ethernet0/0 from the interface list, and click Edit. In the Interface Configuration dialog, configure the options as below:
- Binding zone: Layer 3 zone
- Zone: trust
- Type: Static IP
- IP address: 192.168.1.2
- Netmask: 255.255.255.0
- Click OK to save your settings and return to the Network page.
- Select ethernet0/1 from the interface list, and click Edit. In the Interface Configuration dialog, configure the options as below:
- Binding zone: Layer 3 zone
- Zone: untrust
- Type: Static IP
- IP address: 1.1.1.2
- Netmask: 255.255.255.0
- Click OK to save your settings and return to the Network page.
- Click New, and select Tunnel Interface from the drop-down list. In the Interface Configuration dialog, configure the options as below:
- Name: tunnel1
- Binding zone: Layer 3 zone
- Zone: trust
- Click OK to save your settings and return to the Network page.
Step 2: Configure policy rules.
Device A
- On the Navigation pane, click Configure > Security > Policy to visit the Policy page.
- Click New. On the Basic tab in the Policy Configuration dialog, configure the options as below:
- Src zone: trust
- Src address: Any
- Dst zone: trust
- Dst address: Any
- Service: Any
- Action: Permit
- Click OK to save your settings. The configured policy will be displayed in the policy list below.
- Click New. On the Basic tab in the Policy Configuration dialog, configure the options as below:
- Src zone: untrust
- Src address: Any
- Dst zone: trust
- Dst address: Any
- Service: Any
- Action: Permit
- Click OK to save your settings. The configured policy will be displayed in the policy list below.
Device B
- On the Navigation pane, click Configure > Security > Policy to visit the Policy page.
- Click New. On the Basic tab in the Policy Configuration dialog, configure the options as below:
- Src zone: trust
- Src address: Any
- Dst zone: trust
- Dst address: Any
- Service: Any
- Action: Permit
- Click OK to save your settings. The configured policy will be displayed in the policy list below.
- Click New. On the Basic tab in the Policy Configuration dialog, configure the options as below:
- Src zone: untrust
- Src address: Any
- Dst zone: trust
- Dst address: Any
- Service: Any
- Action: Permit
- Click OK to save your settings. The configured policy will be displayed in the policy list below.
Step 3: Configure Phase1 Proposal.
Device A
- On the Navigation pane, click Configure > Network > IPSec VPN to visit the IPSec VPN page.
- On the Phase1 Proposal tab, click New. In the Phase1 Proposal Configuration dialog, configure the options as below:
- Proposal name: P1
- Authentication: RSA-Signature
- Hash: SHA
- Encryption: 3DES
- DH group: Group2
- Lifetime: 86400
- Click OK to save your settings. The configured proposal will be displayed in the proposal list below.
Device B
- On the Navigation pane, click Configure > Network > IPSec VPN to visit the IPSec VPN page.
- On the Phase1 Proposal tab, click New. In the Phase1 Proposal Configuration dialog, configure the options as below:
- Proposal name: P1
- Authentication: RSA-Signature
- Hash: SHA
- Encryption: 3DES
- DH group: Group2
- Lifetime: 86400
- Click OK to save your settings. The configured proposal will be displayed in the proposal list below.
Step 4: Configure PKI.
Device A
- Select Objects > PKI from the menu bar.
- On the Key tab in the PKI Management dialog, click New. In the PKI Key Configuration dialog, configure the options as below:
- Label: 111
- Type: rsa
- Modulus: 1024
- Click OK to save your settings and return to the PKI Management dialog.
- Click the Trust Domain tab, and then click New on the upper-left. In the PKI Key Configuration dialog, configure the options as below:
- Type td1 into the Trust domain box, and click Manual enrollment in Enrollment type. Click Next to import a CA root certificate.
- Click Browse to select a certificate, and then click Import. Click Next to continue.
- Select 111 from the Key pair drop-down list, and configure the Subject as below:
- Name: aa
- Country (Region): cn
- Locality: hd
- State/Province: bj
- Organization: abc
- Organization unit: rd
- Click Enroll to apply for a local certificate from the CA server. If succeeded, click Import in the Local certificate section to import the local certificate.
- Click Next to configure CRL options as below in the next page:
- Check: Force
- Auto refresh: Daily
- URL1: CA server's address
- Click OK to save your settings.
Device B
- Select Objects > PKI from the menu bar.
- On the Key tab in the PKI Management dialog, click New. In the PKI Key Configuration dialog, configure the options as below:
- Label: 222
- Type: rsa
- Modulus: 1024
- Click OK to save your settings and return to the PKI Management dialog.
- Click the Trust Domain tab, and then click New. In the PKI Key Configuration dialog, configure the options as below:
- Type td2 into the Trust domain box, and click Manual enrollment in Enrollment type. Click Next to import a CA root certificate.
- Click Browse to select a certificate, and click Import. Click Next to continue.
- Select 222 from the Key pair drop-down list, and configure the Subject as below:
- Name: aa
- Country (Region): cn
- Locality: hd
- State/Province: bj
- Organization: abc
- Organization unit: rd
- Click Enroll to apply for a local certificate from the CA server. If succeeded, click Import in the Local certificate section to import the local certificate.
- Click Next to configure CRL options as below in the next page:
- Check: Force
- Auto refresh: Daily
- URL1: CA server's address
- Click OK to save your settings.
Step 5: Configure ISAKMP gateways.
Device A
- On the Navigation pane, click Configure > Network > IPSec VPN to visit the IPSec VPN page.
- On the VPN Peer List tab, click New. In the Peer Configuration dialog, configure the options as below:
- Peer name: east
- Interface: ethernet0/1
- Mode: Main
- Type: Static IP
- Peer address: 1.1.1.2
- Local ID: ASN1-DN
- Peer ID: ASN1-DN,CN=bb,OU=rd,O=abc,L=hd,ST=bj,C=cn
- Proposal 1: p1
- Trust zone: td1
- Click OK to save your settings. The configured ISAKMP gateway will be displayed in the peer list below.
Device B
- On the Navigation pane, click Configure > Network > IPSec VPN to visit the IPSec VPN page.
- On the VPN Peer List tab, click New. In the Peer Configuration dialog, configure the options as below:
- Peer name: east
- Interface: ethernet0/1
- Mode: Main
- Type: Static IP
- Peer address: 1.1.1.1
- Local ID: ASN1-DN
- Peer ID: ASN1-DN,CN=aa,OU=rd,O=abc,L=hd,ST=bj,C=cn
- Proposal 1: p1
- Trust zone: td2
- Click OK to save your settings. The configured ISAKMP gateway will be displayed in the peer list below.
Step 6: Configure Phase2 Proposal.
Device A
- On the Navigation pane, click Configure > Network > IPSec VPN to visit the IPSec VPN page.
- On the Phase2 Proposal tab, click New. In the Phase2 Proposal Configuration dialog, configure the options as below:
- Proposal name: P2
- Protocol: ESP
- Hash 1: SHA
- Encryption 1: 3DES
- Click OK to save your settings. The configured proposal will be displayed in the proposal list below.
Device B
- On the Navigation pane, click Configure > Network > IPSec VPN to visit the IPSec VPN page.
- On the Phase2 Proposal tab, click New. In the Phase2 Proposal Configuration dialog, configure the options as below:
- Proposal name: P2
- Protocol: ESP
- Hash 1: SHA
- Encryption 1: 3DES
- Click OK to save your settings. The configured proposal will be displayed in the proposal list below.
Step 7: Configure a tunnel named VPN.
Device A
- On the Navigation pane, click Configure > Network > IPSec VPN to visit the IPSec VPN page.
- Click New. In the IKE VPN Configuration dialog, click Import behind the Peer name box, and select east from the drop-down list.
- Click Step 2: Tunnel to configure the options for the VPN tunnel as described below:
- Name: VPN
- Mode: tunnel
- P2 proposal: P2
- Proxy ID: Manual
- Local IP/netmask: 10.1.1.0/24
- Remote IP/netmask: 192.168.1.0/24
- Service: Any
- Click OK to save your settings. The configured tunnel will be displayed in the IKE VPN list below.
- On the Navigation pane, click Configure > Network > Network to visit the Network page.
- Select tunnel1 from the interface list, and click Edit. On the General tab in the Interface Configuration dialog, configure the options as below in the Tunnel binding section:
- Tunnel type: IPSec
- VPN name: VPN
- Click OK to save your settings and return to the Network page.
Device B
- On the Navigation pane, click Configure > Network > IPSec VPN to visit the IPSec VPN page.
- Click New. In the IKE VPN Configuration dialog, click Import behind the Peer name box, and select east from the drop-down list.
- Click Step 2: Tunnel to configure the options for the VPN tunnel as described below:
- Name: VPN
- Mode: tunnel
- P2 proposal: P2
- Proxy ID: Manual
- Local IP/netmask: 192.168.1.0/24
- Remote IP/netmask: 10.1.1.0/24
- Service: Any
- Click OK to save your settings. The configured tunnel will be displayed in the IKE VPN list below.
- On the Navigation pane, click Configure > Network > Network to visit the Network page.<</li>
- Select tunnel1 from the interface list, and click Edit. On the General tab in the Interface Configuration dialog, configure the options as below in the Tunnel binding section:
- Tunnel type: IPSec
- VPN name: VPN
- Click OK to save your settings and return to the Network page.
Step 8: Configure routes.
Device A
- On the Navigation pane, click Configure > Network > Routing to visit the Routing page.
- Click New. In the Destination Route Configuration dialog, configure the options as below:
- Destination: 192.168.1.0
- Subnet mask: 255.255.255.0
- Next hop: Interface
- Interface: tunnel1
- Click OK to save your settings. The configured route will be displayed in the route list below.
Device B
- On the Navigation pane, click Configure > Network > Routing to visit the Routing page.
- Click New. In the Destination Route Configuration dialog, configure the options as below:
- Destination: 10.1.1.0
- Subnet mask: 255.255.255.0
- Next hop: Interface
- Interface: tunnel1
- Click OK to save your settings. The configured route will be displayed in the route list below.

