IPS Configuration Example
This section describes how to configure IPS via WebUI by giving you several configuration examples, including:
- Protecting critical services in an Intranet
- Protecting an enterprise's Intranet
- Isolating intrusions in an enterprise's Intranet
Note: Do not use CLI and WebUI to configure IPS at the same time. Choose only one method.
Protecting Critical Services in an Intranet
The goal is to configure an IPS rule that protects Web Server, Mail Server and DNS Server within an Intranet against external attacks.
The network layout is: Hillstone device's ethernet0/1 is connected to Internet in the untrust zone; the ethernet0/0 is in the trust zone; the Web Server, Mail Server and DNS Server are connected to the Hillstone device on etherent0/0. The topology is shown as below:
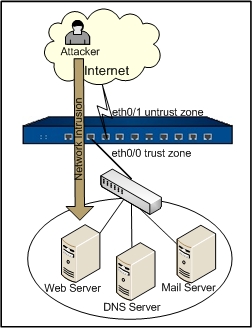
For more information on the configuration of interfaces and security zones, see other related sections. This section only describes how to configure IPS. Take the following steps:
Step 1: Configure a service group used for policy rule reference.
- Select Objects > Service Book from the menu bar.
- In the Service Book dialog, click New, and select Service Group from the drop-down list. In the Service Group Configuration dialog, configure the options as below:
- Name: ips-service
- Description: IPS service group
- Member: Select HTTP from the Available list, and click Add> to add to the Selected list. Use the same steps to add SMTP, POP3 and DNS.
- Click OK to save your settings and return to the Service Book dialog. Click
 to close the dialog.
to close the dialog.
Step 2: Configure an IPS rule.
- On the Navigation pane, click Configure > Security > IPS to visit the IPS page.
- Click New on the upper-left of the rule list. In the IPS Configuration dialog, configure the options as below:
- Rule name: server-protection
- Binding zone: trust
- Direction: Click Bi-direction, and click Add.
- Protocol types: Select DNS, POP3, SMTP and HTTP.
- Click OK to save your settings and return to the IPS page.
- In the server-protection rule, click SMTP under the Protocol type column, and configure other options for SMTP protocol in the SMTP Signature DB page. This section only takes Action for brute-force for example. Configure the options as below:
- Brute-force: Select the Enable check box.
- Login threshold per min: 10
- Block by: Attacker IP
- Block duration: 300
- Click OK to save your settings.
Step 3: Configure a policy rule.
- On the Navigation pane, click Configure >Security > Policy to visit the Policy page.
- Click New. In the Policy Configuration dialog, configure the options as below:
- Src zone: untrust
- Src address: any
- Dst zone: trust
- Dst address: any
- Service: ips-service
- Action: Permit
- Click OK to save your settings.
Protecting Enterprise's Intranet
The goal is to configure an IPS rule that protects an Intranet against external intrusions.
The network layout is: Hillstone device's ethernet0/1 is connected to Internet in the untrust zone; the ethernet0/0 is connected to an Intranet in the trust zone. The topology is shown as below:
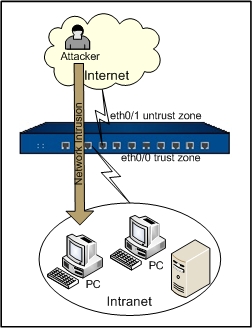
For more information on the configuration of interfaces and security zones, see other related sections. This section only describes how to configure IPS. Take the following steps:
- On the Navigation pane, click Configure > Security > IPS to visit the IPS page.
- Click New on the upper-left of the rule list. In the IPS Configuration dialog, configure options as below:
- Rule name: intranet-protection
- Binding zone: trust
- Direction: Click Inbound, and click Add.
- Protocol types: Click Select All
- Click OK to save your settings and return to the IPS page.
Isolating Intrusions in an Enterprise's Intranet
The goal is to configure an IPS rule that isolates intrusions in an Intranet.
The network layout is: the Development, Production and Marketing departments of an enterprise belong to 3 segments; the above 3 segments are connected to a Hillstone device on ethernet0/2, ethernet0/3 and ethernet0/4 respectively, and the binding zones of the 3 interfaces are named Development, Production and Marketing respectively; the device's ethernet0/1 is connected to Internet in the untrust zone. The topology is shown as below:
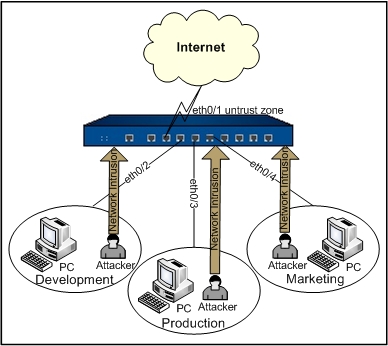
For more information on the configuration of interfaces and security zones, see other related sections. This section only describes how to configure IPS. Take the following steps:
- On the Navigation pane, click Configure > Security > IPS to visit the IPS page.
- Click New on the upper-left of the rule list. In the IPS Configuration dialog, configure options as below:
- Rule name: intranet-protection
- Select Development from the Binding zone drop-down list, click Bi-direction in Direction, and then click Add. Use the same steps to add Production and Marketing security zones.
- Protocol types: Click Select All
- Click OK to save your settings and return to the IPS page.



