Last week, Microsoft released its July security update patch. A vulnerability reported by three security researchers from the Hillstone Security Research Team was amended, and an acknowledgement message was issued on the official website classified under vulnerability number CVE-2021-33774.
A memory corruption vulnerability in the implementation of the Event Tracing function was discovered in the Windows kernel. Attackers could potentially exploit this vulnerability to alter access privileges. The vulnerability level hence classified as “important.”
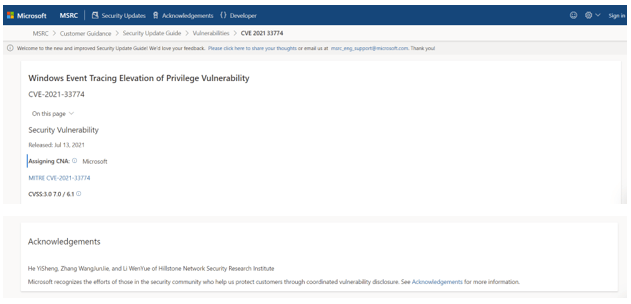
This month’s security updates fixes a total of 117 vulnerabilities. Including 13 high-risk vulnerabilities, 102 serious vulnerabilities, 1 medium-risk vulnerability, and 1 low-risk vulnerability, covering components such as Windows operating system, Exchange Server, Azure, Office, SharePoint Server, Hyper-V, and Visual Studio. The risks are wide-ranging and consequential. It is recommended that users update the patches in a timely manner.
Hillstone Security Research Team
As a leading provider of Enterprise Network Security and Risk Management solutions, protecting our customers in a proactive way is our highest goal. This is why we deploy a security research team and resources that are dedicated to uncovering vulnerabilities in widely used products globally. We will continue devoting our efforts to safeguarding global network security.
Resources:
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-33774
https://msrc.microsoft.com/update-guide/acknowledgement/cve
https://msrc.microsoft.com/update-guide/releaseNote/2021-Jul



