Introduction
Recently, the details of a remote code execution vulnerability in Apache Log4j2 have been disclosed. Once the vulnerability is exploited by an attacker, it will cause serious harm. The vulnerability has an extremely wide range of impact and can result in serious consequences. We recommend that enterprises initiate an emergency response to repair it immediately.
Apache Log4j2 is an excellent Java log framework. This tool rewrites the Log4j framework and introduces a large number of features. The log framework is commonly incorporated with web service system. The vulnerability leverages the insufficient sanitization of data supplied by user in the domain name or directory lookup service to potentially allow attackers to construct malicious requests to trigger remote code execution vulnerabilities.
Affected Version
2.0 <= Apache Log4j <= 2.15.0-rc1
Defense and Fix Suggestions
Vulnerability exploitation does not require special configuration. The security team has verified that Apache Struts2, Apache Solr, Apache Druid, Apache Flink, etc. are all affected. Because this component is widely used, Apache Log4j2 users are reminded to take security measures as soon as possible to prevent vulnerability attacks.
Based on the current characteristics of the vulnerability, we recommend the following suggestions:
- Official fix: https://github.com/apache/logging-log4j2/releases/tag/log4j-2.15.0-rc2
- Modify jvm parameter -Dlog4j2.formatMsgNoLookups=true
- Modify configuration log4j2.formatMsgNoLookups=True
- Set the system environment variable FORMAT_MESSAGES_PATTERN_DISABLE_LOOKUPS to true
Hillstone NGFW, NIPS, sBDS can support the detection of the vulnerability. IPS signature database version: 2.1.434/3.0.86. The corresponding signatures: 334337, 334338, 334364.
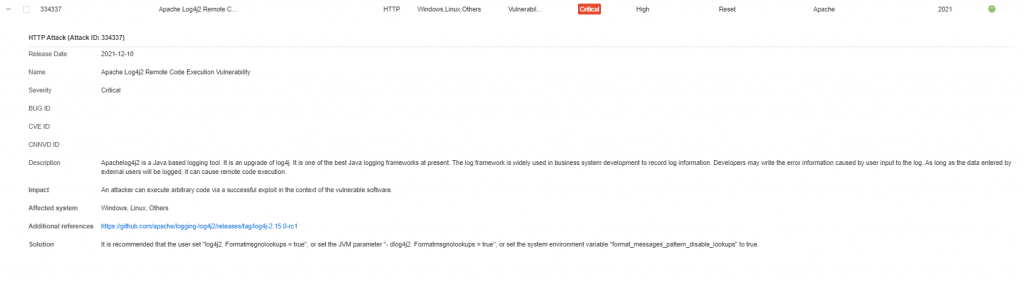
Figure 1. Log4j vulnerability detected by Hillstone NGFW, NIPS, sBDS
Hillstone WAF can support the detection of the vulnerability. WAF signature database version: 1.1.130. The corresponding signature: 1070310151.
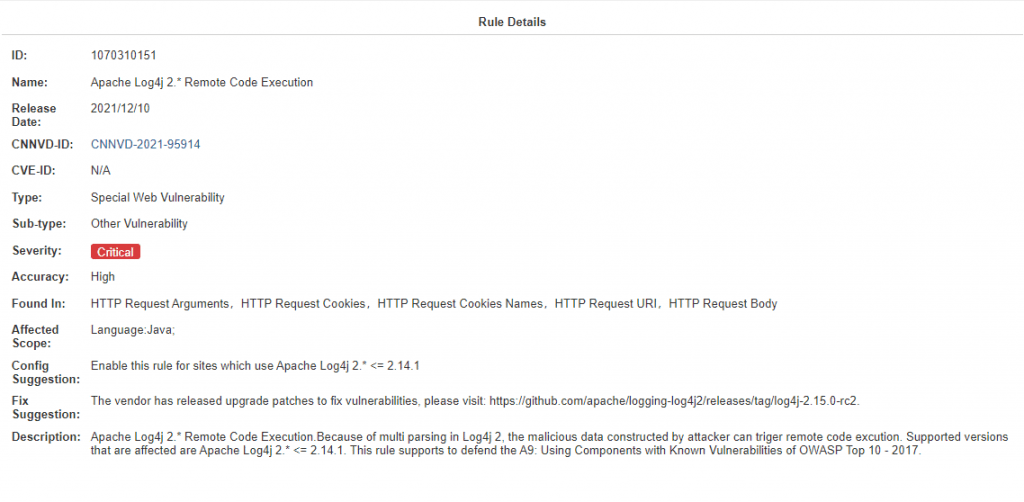
Figure 2. Log4j vulnerability detected by Hillstone WAF
The hotspot intelligence of this vulnerability is available on Hillstone iSource as well.
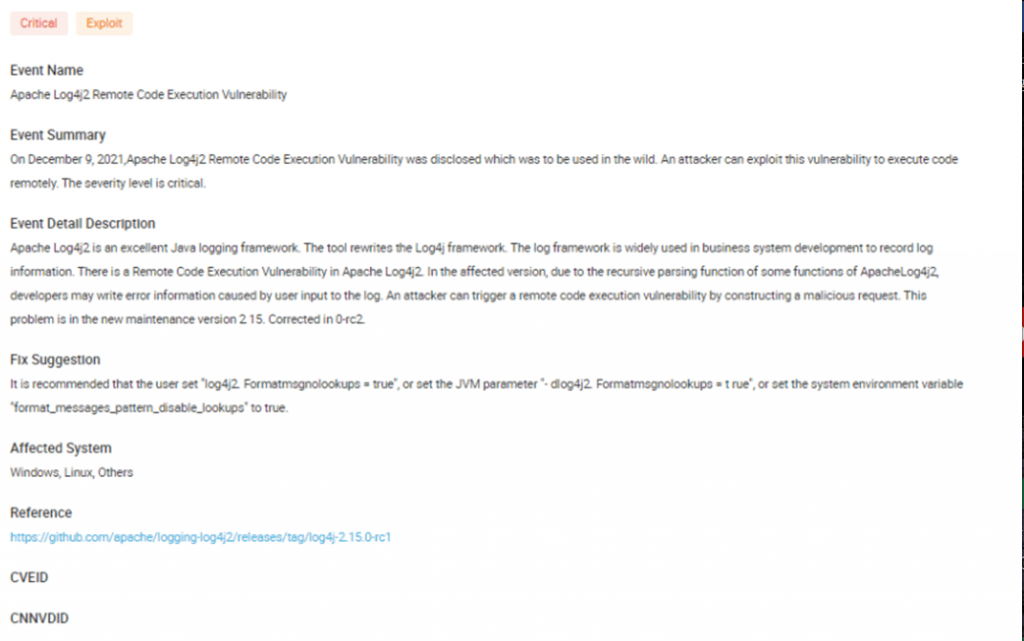
Figure 3. Hotspot intelligence on Hillstone iSource