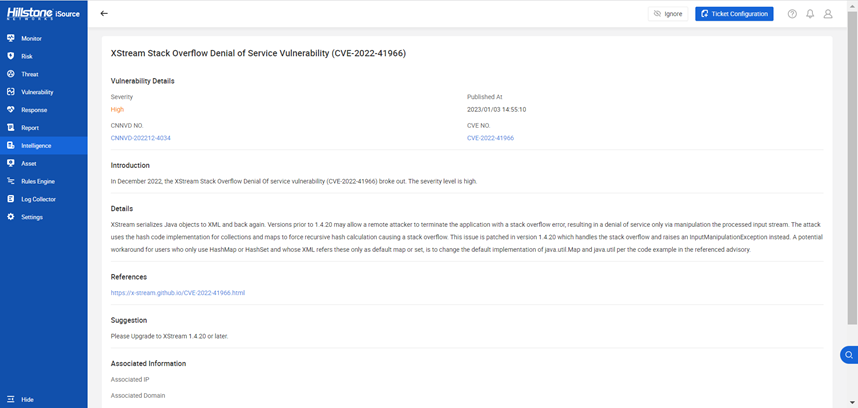
Introduction
XStream is a Java-based library for serializing Java objects to XML and back again. Recently, the highly severe XStream stack overflow denial of service vulnerability emerged. This vulnerability makes it possible for a remote attacker to terminate the application with a stack overflow error, resulting in a denial of service, by manipulating the input stream.
Vulnerability
Users can not only use XStream to marshal Java objects to XML, but also unmarshal XML to Java objects with XStream.
In order to convert XML back into Java objects, XStream needs the type information of the objects included in the stream that is processed during unmarshalling. An attacker can process the input stream, then replace or inject objects. In that way, As soon as the XML gets unmarshalled, the recursive hash calculation is entered, and the executing thread is aborted with a stack overflow error, leading to a denial of service.
Affected Version
XStream <= 1.4.19
Remediation
1. Official fix: The vendor has released the patches, and we recommend that users upgrade to XStream 1.4.20 or a later version. Please visit:
http://x-stream.github.io/download.html
2. Workarounds on GitHub: Mitigate this risk by catching the StackOverflowError in the client code calling XStream. Please visit:
https://github.com/advisories/GHSA-j563-grx4-pjpv
Implementing the Fix
The Hillstone Networks Intrusion Prevention System (IPS) and Hillstone Server Breach Detection System (sBDS) can support the detection and protection of this vulnerability.
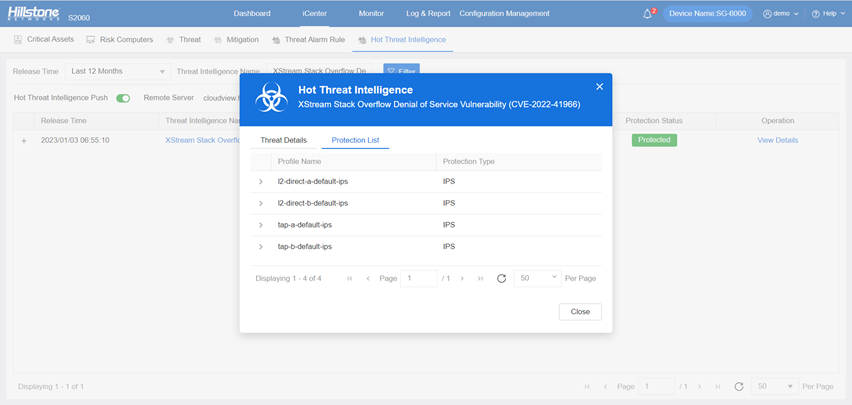
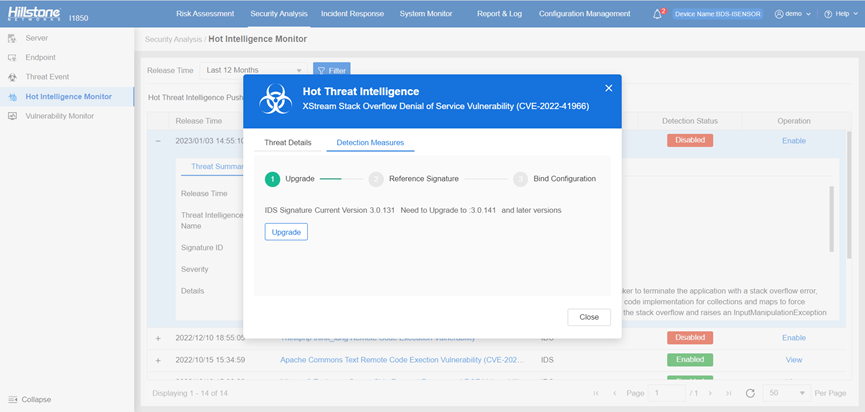
The hotspot intelligence of this vulnerability is available on Hillstone Networks iSource as well.