Introduction
“Your network is encrypted by the Black Basta group.” “The data will be published on TOR website if you do not pay the ransom…” Ransomware. This is the word that sends chills down the spine. In this age of ransomware, sensitive data is hijacked, and only returned upon the delivery of a monetary demand. The Black Basta, originally discovered in April 2022, is a new and rampantly spreading family of ransomware. In just a few months, this newcomer has extended its reach to over 50 companies worldwide. At the moment, these attacks appear to be industry-agnostic, with reported infiltrations in multiple verticals and industries.
Vulnerability
Recently, Black Basta’s ransomware has made use of Qakbot (QBot), a tool that leverages Windows Management Instrumentation (WMI) to interact directly with the operating system and collect actionable information. One such example is using QBot to discover and screen the installed endpoint security software to magnify its weakness, for which payloads can be purposefully inserted into the device. On the top of this, Black Basta can loot sensitive data and run malicious payloads.
With the help of QBot, Black Basta’s attack plan is usually as follows:
First, the attackers harvest credentials and understand the network architecture. From there, they target the Domain Controller (DC), and move laterally using PsExec. Once the DCs are successfully compromised, a Group Policy Object is created to disable Windows Defender, and it will proceed to take down any anti-virus products.
The next stage of the attack is to deploy the ransomware to the targeted endpoints through an encoded PowerShell command. Afterwards, the final payload — the Black Basta ransomware — is successfully implanted on the victim’s machine. As is common with ransomware, Black Basta will encrypt the files on the machine, and leave a ransom note to the user. When the payload is eventually executed, the ransomware first deletes the system’s Virtual Volume Shadow Copies (VSS) and other backups of files, ensuring victims cannot decrypt or retrieve files from VSS.
As far as the ransomware’s encryption routine, it begins the process by turning the background of the desktop into a black image with the words written above. At the same time, it will go through the files and encrypt them, adding the extension “.basta” to the encrypted files. Finally, the ransom note named “readme.txt” is customized with a unique id, which can be found in an arbitrary folder for the victim to use in negotiations with Black Basta.
Remediation
To prevent the execution of the Black Basta ransomware, we have a cyber-resilient mitigation strategy for building a multi-layer defense protocol that’ll detect and block malware using a combination of threat intelligence, machine learning, and next-gen antivirus (NGAV) capabilities.
Our mitigation strategy creates a monitoring method that can identify known and unknown malware variants, and can block and generate a MalOpTM for any attempt to encrypt files as soon as it is detected. To execute this strategy, a few prerequisites need to be met:
- Enable the anti-ransomware feature on your NGAV
- Enable the anti-malware feature on your NGAV
- Keep systems fully patched
- Regularly backup files to a remote or offsite server
- Use security solutions with organizational devices and methods
Implementing the Fix
Hillstone botnet detection signature database can provide adequate protection against this vulnerability. Devices, such as Hillstone sBDS, can automatically activate and deploy this ability via an update to the newest version 3.8.220728.
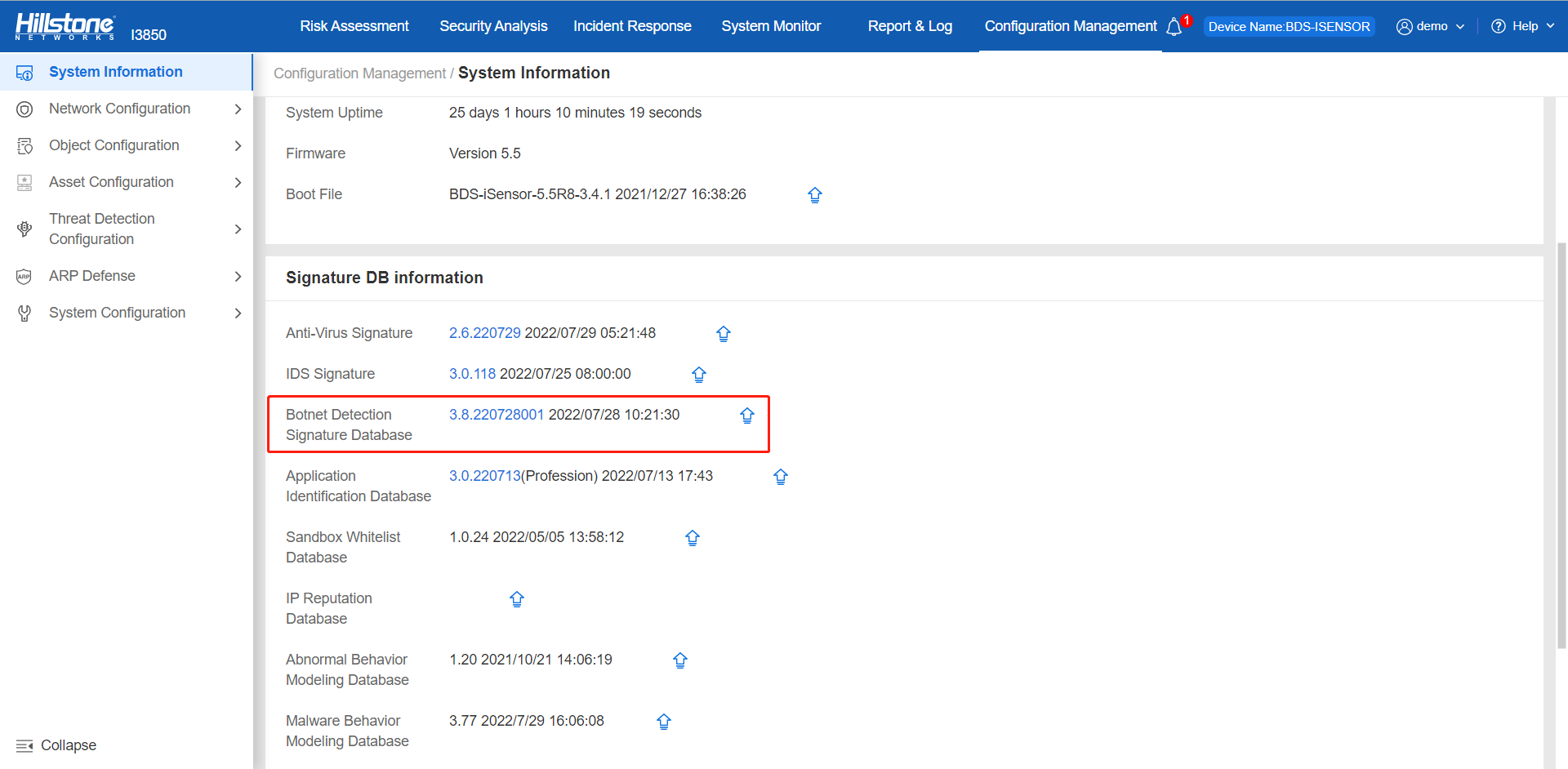
Figure 1. The Black Basta configured the defense against by Hillstone botnet detection signature database in sBDS



