Introduction
F5 BIG-IP is an application delivery platform of F5, which provides network traffic management, application security management, load balancing and other functions. As a collection of hardware platforms and software solutions, F5 BIG-IP was found to possess an access control error vulnerability, CVE-2022-1388, which could be exploited by attackers.
Vulnerability
When vulnerability CVE-2022-1388 is exploited, an attacker can take control of the system anonymously by bypassing the iControl Representational State Transfer (REST) authentication framework. Specifically, in BIG-IP versions that are between 12.x and 16.x, attackers can exploit CVE-2022-1388 through the management port and/or self IP addresses to gain unauthorized network access to the BIG-IP system. From there, attacks can execute arbitrary system commands, create or delete files, or disable services. There is no data plane exposure; this is a control plane issue only. Horizontal and vertical privilege escalation is a common tactic of exploiting vulnerabilities. Upon gaining a foothold, attackers leverage these tactics to elevate their access privileges illegally. As such, it is critical that we stay vigilant, both in terms of securing these vulnerabilities quickly, and ensuring we have flexible post-breach mitigation strategies in place.
Remediation
The remediation strategy has arrived and users can eliminate this vulnerability by upgrading to the new corresponding version. While installation of an updated version is a guaranteed fix, users can use the following recommendations as temporary mitigations. These mitigations restrict access to iControl REST to only trusted network or devices, thereby restricting the attack surface.
- Block iControl REST access through self-defined IP address
- Block iControl REST access through the management interface
- Modify the BIG-IP httpd configuration
Implementing the Fix
Hillstone IPS can provide adequate protection against this vulnerability, and the protection can be automatically configured within the device by updating the signature database version to 3.0.107, 2.1.456, with no or very few false positives. The corresponding rule to remediate this vulnerability is rule 336580.
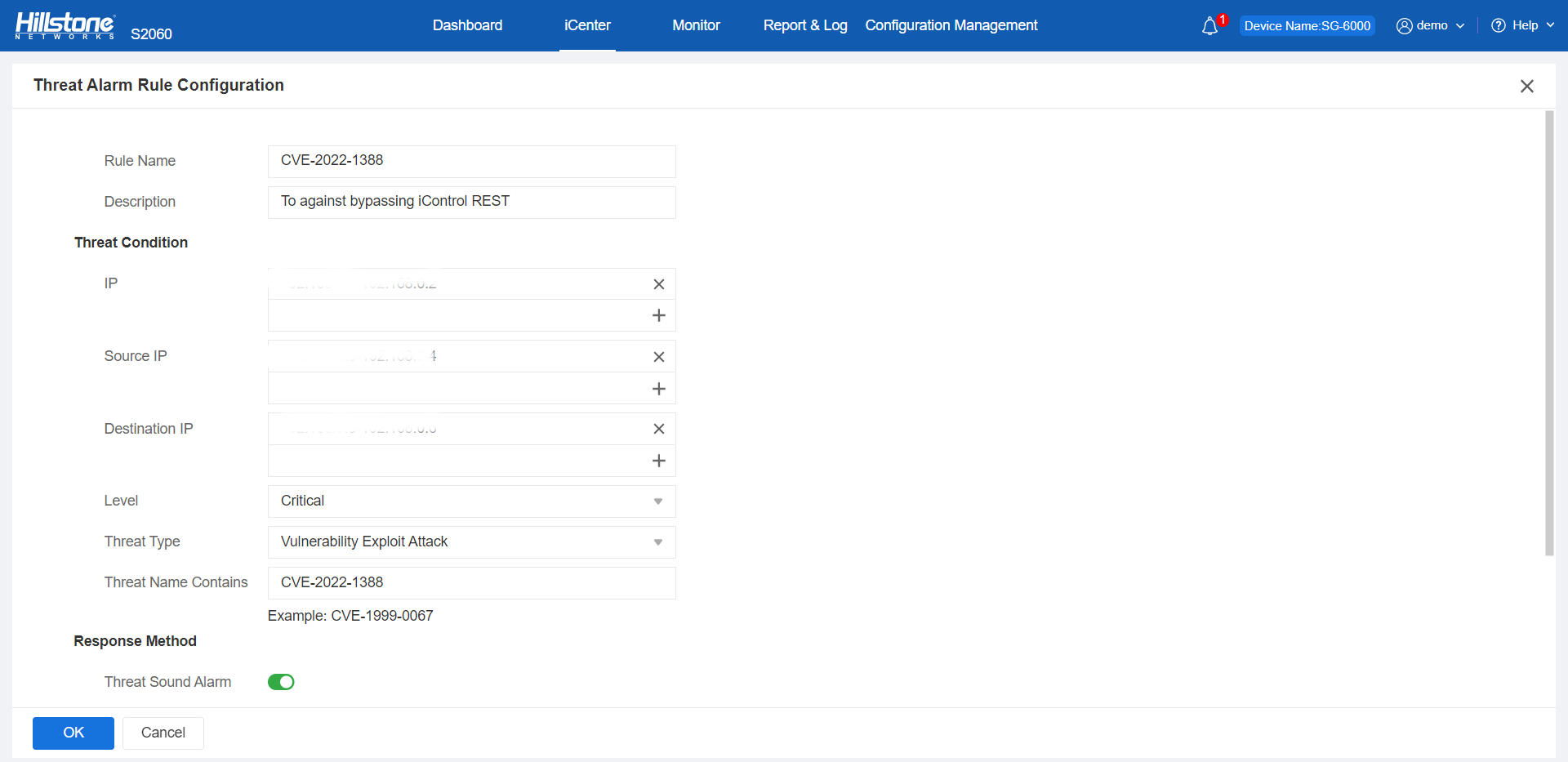
Figure 1. CVE-2022-1388 configured the defense against by Hillstone IPS
The hotspot intelligence of this vulnerability is available on Hillstone iSource as well.
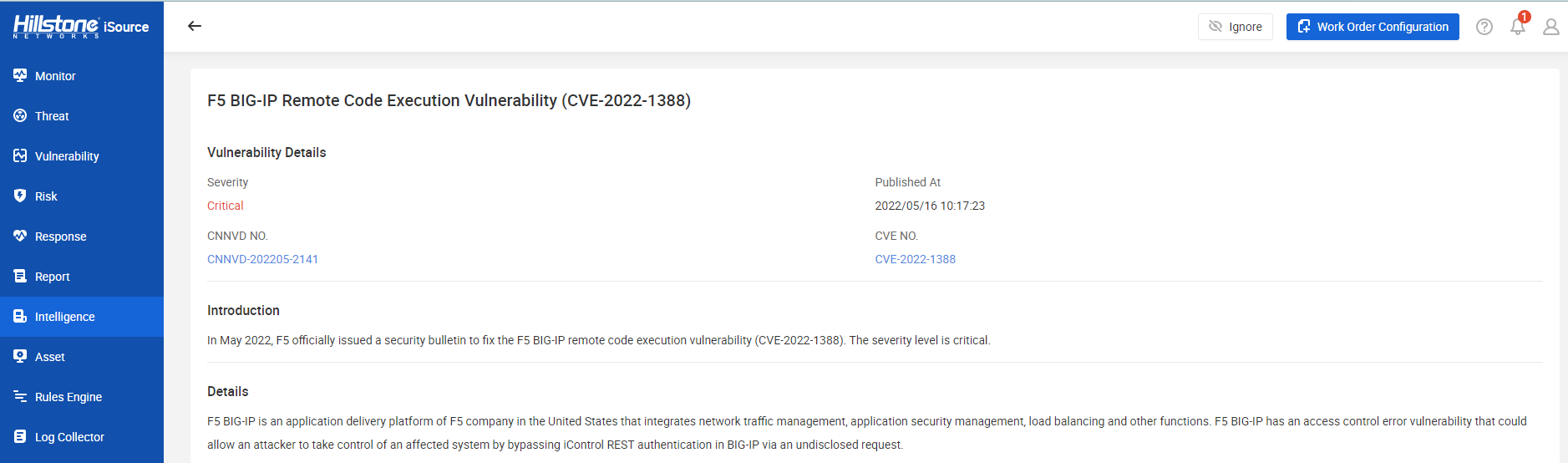
Figure 2. Hotspot intelligence on Hillstone iSource



