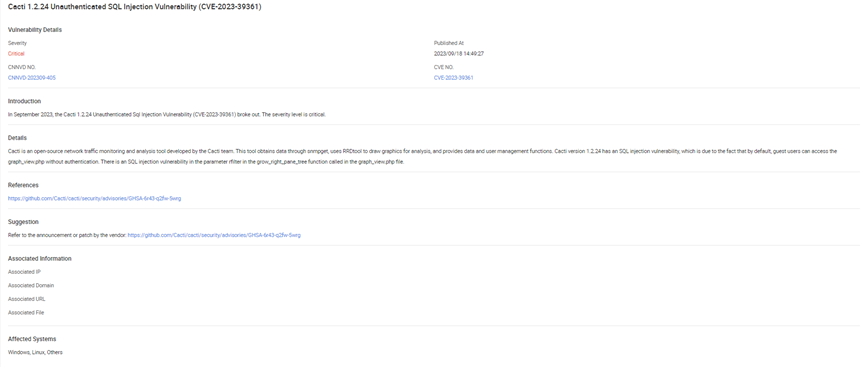
Introduction
Cacti, an open-source tool developed by the Cacti team, has long been a trusted resource for network traffic monitoring and analysis. However, as with any software, vulnerabilities can arise. One such vulnerability that demands immediate attention is the Cacti Unauthenticated SQL Injection Vulnerability.
Vulnerability
SQL injection is a commonly encountered type of vulnerability that occurs when user input is not properly sanitized, enabling attackers to inject malicious SQL code into an application’s database queries. In the context of Cacti 1.2.24, the vulnerability is related to the ‘graph_view.php’ page, accessible to guest users without authentication by default.
The vulnerability is specifically found in the ‘rfilter’ parameter within the ‘grow_right_pane_tree’ function called from the ‘graph_view.php’ file. This parameter is not properly validated, and an attacker can manipulate it to inject malicious SQL code into the application’s database.
Once exploited, this vulnerability could allow an attacker to seize administrative privileges or execute remote code, resulting in unauthorized control and access to the system.
Affected Version
Cacti version 1.2.24
Remediation
Official fix: To prevent these attacks, users are recommended to upgrade to version 1.2.25 and version 1.3.0. Please visit:https://forums.cacti.net/viewtopic.php?p=292797#p292797
Implementing the Fix
Upgrade your IPS signature database to version 3.0.175 and your AV signature database to version 2.1.525 to ensure that Hillstone Networks Intrusion Prevention System (NIPS) and Hillstone Breach Detection System (BDS) are equipped to detect and provide protection against this vulnerability.
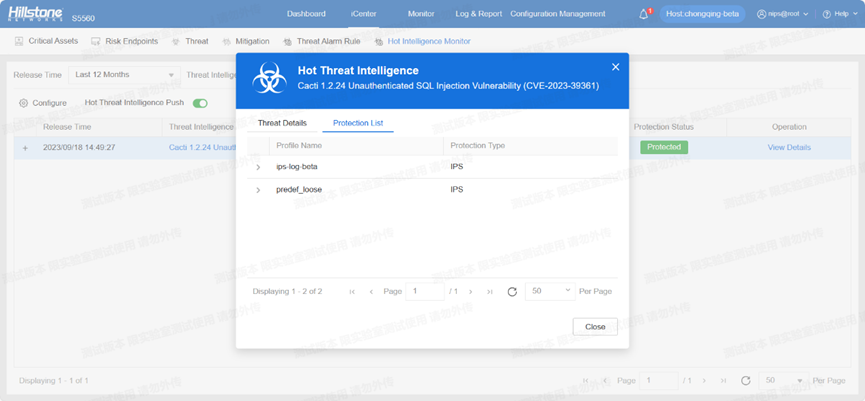
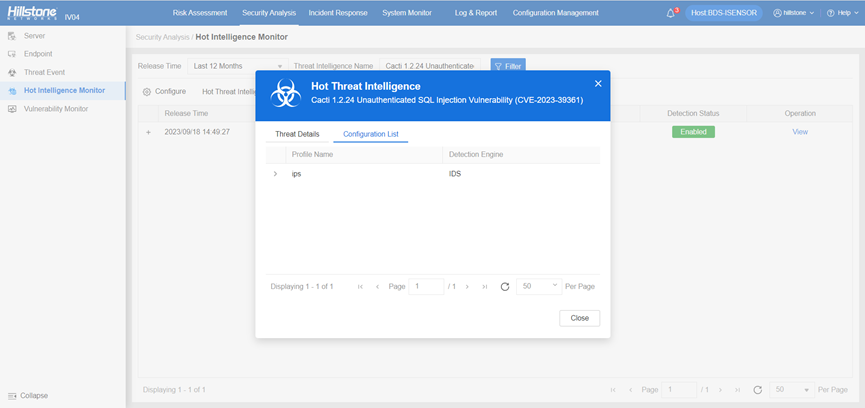
The hotspot intelligence of this vulnerability is available on Hillstone Networks iSource as well.