Application Modernization
The IT landscape has transformed digitally beyond our recognition during the COVID-19 pandemic which forced many businesses and organizations to speed up their transformation process. When undergoing a metamorphosis, a key element of a digital business is its application. It does not make sense that IT organizations operate on entirely digital IT systems, yet still rely on monolithic outdated operation systems. Old monolithic applications cannot provide the agility and flexibility required in this digital age.
It is difficult for legacy applications to integrate the new modern technologies like AI, loT, and Cloud. This proves to be a problem because these contemporary technologies can deliver computing services including servers, storage, databases, networking, software, analytics, and intelligence over the internet. Enterprises running on legacy infrastructures will miss out on opportunities for offering faster innovation, flexible resources and economies of scale. Legacy applications lack flexibility and prevent many organizations from threat correlation, advanced analytics, and a rich digital experience.
So, application modernization is the key to digital transformation and boosting the business.
Why Microservices
What’s more, new technologies are built on microservices cloud architecture, no matter private or public cloud, which also driving legacy upgrades. Hence, many business and organizations modernize their applications by rearchitecting and refactoring the applications into multi-microservices by segmenting pieces of functionality and running them as independent units. this decoupling allows more flexibility since each service is independent and can be developed, deployed, and maintained separately from the other services.
- Resilience: For a monolithic application, a single error in the code may bring the entire application down, but with microservices, this can be avoided since your application is decentralized and segmented into many micro services. Even if some services are down, users may not necessarily be impacted.
- Scalability: Each microservice is independent and easy to scale up/down without having to scale the entire application. This is more reasonable to increase some services’ performance without impacting other services.
- Faster to release: Each microservice can be developed and maintained by a small team. A change in code does not involve other services, and would only require small-scale functional testing. Upon that, the latest version of the service can be deployed online swiftly.
- Easy upgrade and deployment: Cloud platforms provides various methods of zero system downtime during upgrades. At times, old and new versions can run simultaneously.
Microservices provide us a better way to modernize our applications.
Containerized microservices
Containers virtualize multiple application runtime environments on the same operating system instance. With this added convenience, it doesn’t need to contain a separate OS image like VMs do, so this makes containers lightweight and portable, vastly reducing the requirement of system resource availability and usage. Each microservice running on its own physical or virtual machine is wasteful, and most of them just require a small amount of system resources, so containerized microservices work perfectly here. A growing trend of automating deployment, scaling, orchestration and management of containerized microservices give businesses the freedom to take advantage of on-premise, hybrid, and public cloud infrastructures, allowing for effortless migration of workloads as needed.
Cloud workload protection platform (CWPP)
First things first. The cloud workload protection platform solution is used to discover workloads (containerized microservices) that exist within an organization’s cloud-based deployments or on-premise infrastructure. After completing the asset discovery and modeling process, a CWPP then performs a comprehensive risk assessment to identify any potential security issues, and with the ability to wield granular control over the traffic between workloads, delineates actions as necessary.
Workload protection is different from application security. The only security holes in applications exist as vulnerabilities within its code, whereas the rest of the environment can be secured via other means. Cloud-based workloads, however, may potentially be deployed in the public cloud, which is outside of the organization’s jurisdiction. As such, in these scenarios, CWPP is critical to provide the runtime activity monitor, vulnerability scan, integrity protection, compliance, threat hunting, and security controls to deduce and mitigate the risk.
During the process of application modernization, services/applications may face a myriad of threats throughout the entire DevOps lifecycle.
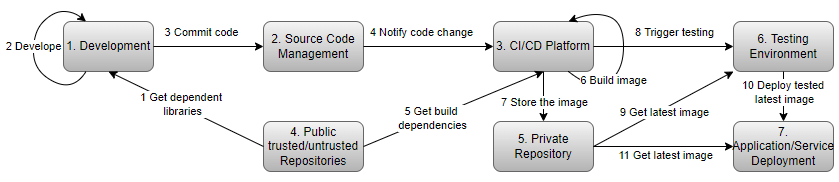
Hillstone workload protection platform
Cloud-based workloads don’t work independently. They will access and perform data exchanges amongst each other, meaning if any of the workloads are compromised, it may infect other workloads. Even more concerning is the fact that we do not know which workload has accessed which other workloads. It is essence, like trying to backtrack where the spread of a virus began. Secure DevOps, also known as DevSecOps, integrates the evaluation of vulnerability, and security protection into the lifecycle, from development to production. Hillstone CloudArmour Production focus on this area and helps your application/service run on a secure and sanitized environment.
Some of the CWPP vendors only provide workload protection in the cloud or virtual machine environments respectively, but Hillstone CloudArmour supports a hybrid mode. it can manage and secure your organization’s applications and hosts (bare metal or virtual machine), regardless if they are located in on-premise or public cloud.
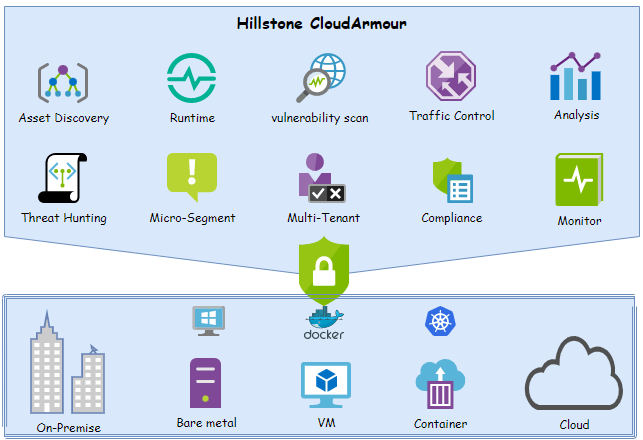
- Asset Discovery
- Well integrated with Kubernetes, for retrieving workload information and distributing them to thousands of protected nodes instantaneously.
- Discover workloads that are deployed in VM or bare metal machine.
- Asset association
- Runtime Security
- File Protection
- Process activity monitor
- Leverage machine-learning to understand the network activity, process running, and file accessing behavior to building a model for halting abnormal behavior.
- L4 & L7 Application isolation
- Traffic Control
- Traffic Control based on L7 workload but not just L4 IP&Port
- Traffic Control between workload and host
- Integrated with Kubernetes. it supports granular access control between Deployment/Service/ReplicaSet/DaemonSet/StatefulSet/Pod resource.
- Vulnerability scan
- Distributing tasks to managed nodes for vulnerability scanning of private/public image repository.
- Vulnerability scanning for just running workload’s image
- Support interception of workload creation and scanning the image. if vulnerability is found, it will report alert event or terminate the creation process, or ignore it and continually create the workload based on customized vulnerability rules.
- Micro-segment
- Network segment
- Workload segment
- Process segment
- File Protection
- Multi-tenant
- Support multi-tenant management based on namespace and application
- Application shared between tenants
- Compliance
- Support Image Compliance check
- Support Application Compliance check
- Support Host Compliance check
- Monitor
- Monitor workload status and compliance result
- Monitor runtime activities and predict the potential risk.
- Threat hunting
- Advanced host threat detection engine
- Customized threat detection rules definition
- Analysis and associate alerts and find out the threat event.
Hillstone CloudArmour delivers the abilities of workload discovery and visibility access, runtime behavior monitoring and intelligence machine-learning, vulnerability scan and advanced threat detection, topped off with compliance checking. By combining all of these capabilities together, CloudArmour provides an advanced holistic risk evaluation and automated mitigation system to help users eliminate potential threats. This keeps workloads running on clean and secure environment. With the migration to micro-services and the threat landscape rapidly continuing to change, enterprises need to plan for protecting their workloads across on-premise and cloud environments. Hillstone CloudArmour will help you see, understand, and act across this space, providing security that works.



