[Overview]
As a next-generation network management software, Zoho OpManager provides network performance monitoring, physical and virtual server monitoring, network traffic analysis, and device management configuration to realize integrated management of the network, server and data center. OpManager has fixed a privilege elevation vulnerability in a recent update.
[Vulnerability Details]
CVE-2018-17283: The vulnerability is caused by a lack of access control for specific method. An unauthenticated attacker could exploit this vulnerability by sending an HTTP request to the /oputilsServlet with the action parameter “getAPIKey” and access the REST API interface with the detected API key.
Successful exploitation of the vulnerability will allow the attacker to take complete control of the OpManager service, causing information disclosure or implementing SQL injection attacks.
Vulnerability Source: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-17283
[Severity]
Critical
[Affected Versions]
Zoho Corporation ManageEngine OpManager prior to 12.3 Build 123196
[Suggestions]
Update the bug fix release provided by OpManager to eliminate the damage caused by the vulnerability.
Official advice: https://www.manageengine.com/network-monitoring/help/read-me.html
[Hillstone Networks Solutions]
Hillstone Networks has added signatures to the IPS signature database version 2.1.259. By deploying any Hillstone Networks solution with the IPS function, Zoho ManageEngine OpManager oputilsServlet Authentication Bypass vulnerability can be quickly detected and effectively intercepted, preventing the server from being attacked.
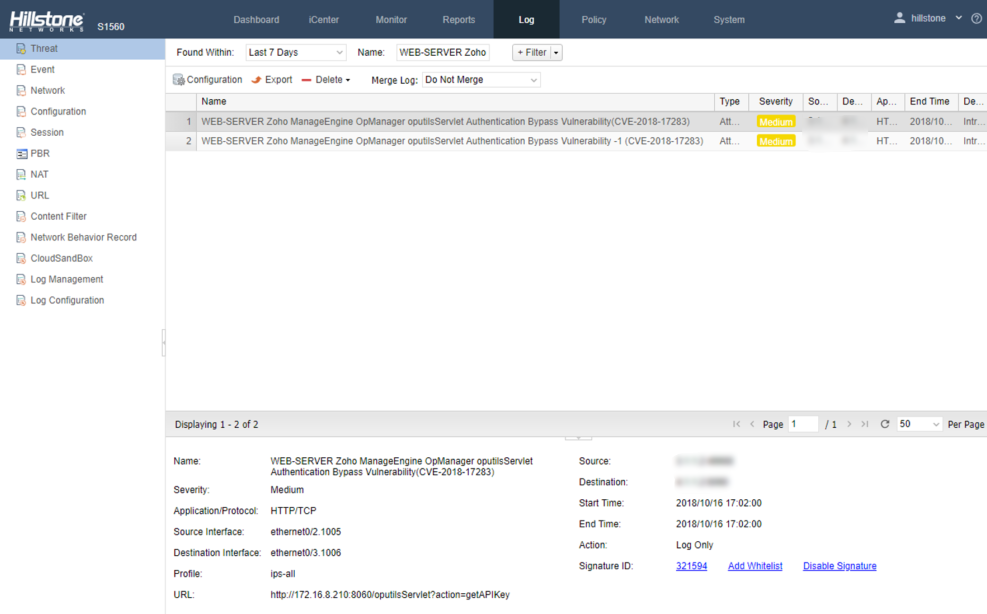
Threat Events Detected by Hillstone Solutions
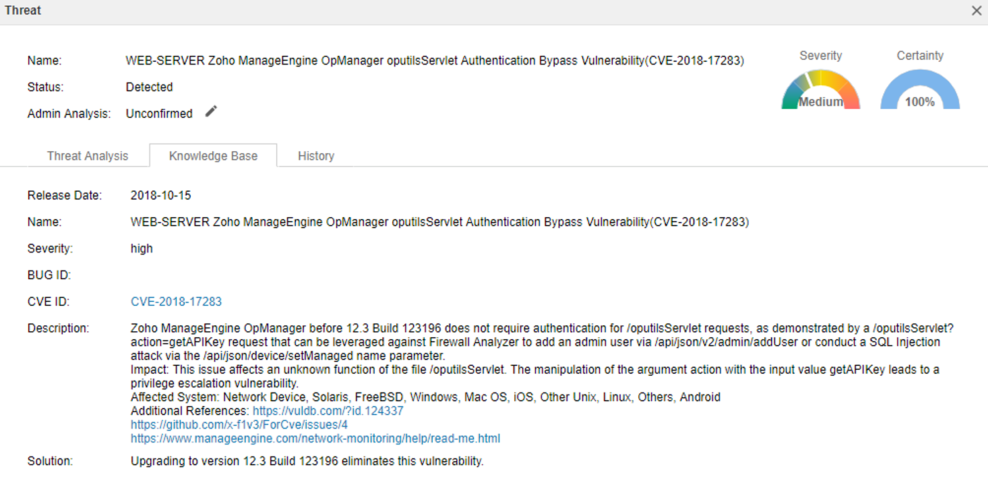
Vulnerability Detail Description


