[Overview]
The SMB protocol is a network sharing protocol used in Microsoft Windows, and is often used to share files and printers within a local area network; SMBv3 is version 3 of SMB. Recently, Microsoft announced an SMBv3 remote code execution vulnerability. At present, Microsoft has released a security patch to fix the vulnerability. Meanwhile, Hillstone Networks has released signatures against this vulnerability. It is recommended that users patch or upgrade the intrusion detection signature database of network security devices in time for protection. Check our SMBGhost Analysis white paper to learn more.
[Vulnerability Details]
CVE-2020-0796: This is a memory corruption vulnerability targeting SMB server/client, which is a serious remote code execution vulnerability. Hackers can use this vulnerability to execute arbitrary code on the target SMB server or SMB client.
The client-side vulnerability occurred in mrxsmb.sys. The server-side vulnerability occurred in srv2.sys. SMB did not properly handle the compressed data packet nor use the length passed by the client for the data packet decompression without checking whether the length is legal, thereby causing an integer overflow.
Vulnerability Source: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-0796
[Severity]
High
[Affected Versions]
- Windows 10 Version 1903 for 32-bit Systems
- Windows 10 Version 1903 for x64-basedSystems
- Windows 10 Version 1903 for ARM64-basedSystems
- Windows Server, version 1903 (Server Core installation)
- Windows 10 Version 1909 for 32-bit Systems
- Windows 10 Version 1909 for x64-basedSystems
- Windows 10 Version 1909 for ARM64-basedSystems
- Windows Server, version 1909 (Server Core installation)
[Suggestions]
- Update the official fixes to avoid being affected by the vulnerability
- If it cannot be updated immediately, temporary mitigation measures should be taken:
- Disable SMBv3 compression; use PowerShell commands to disable compression to prevent unauthenticated attackers from exploiting the vulnerability of the SMBv3 server.
- Close port 445
- The network security device should upgrade the intrusion detection signature database.
[Hillstone Networks Solutions]
Hillstone Networks has added this threat behavior to the signature list, Signature Database Version: 2.1.341. By deploying Hillstone Networks NIPS, NGFW, CloudEdge, CloudHive, or sBDS, the SMBv3 Protocol Remote Code Execution vulnerability can be quickly detected and effectively intercepted, preventing the server from being attacked.
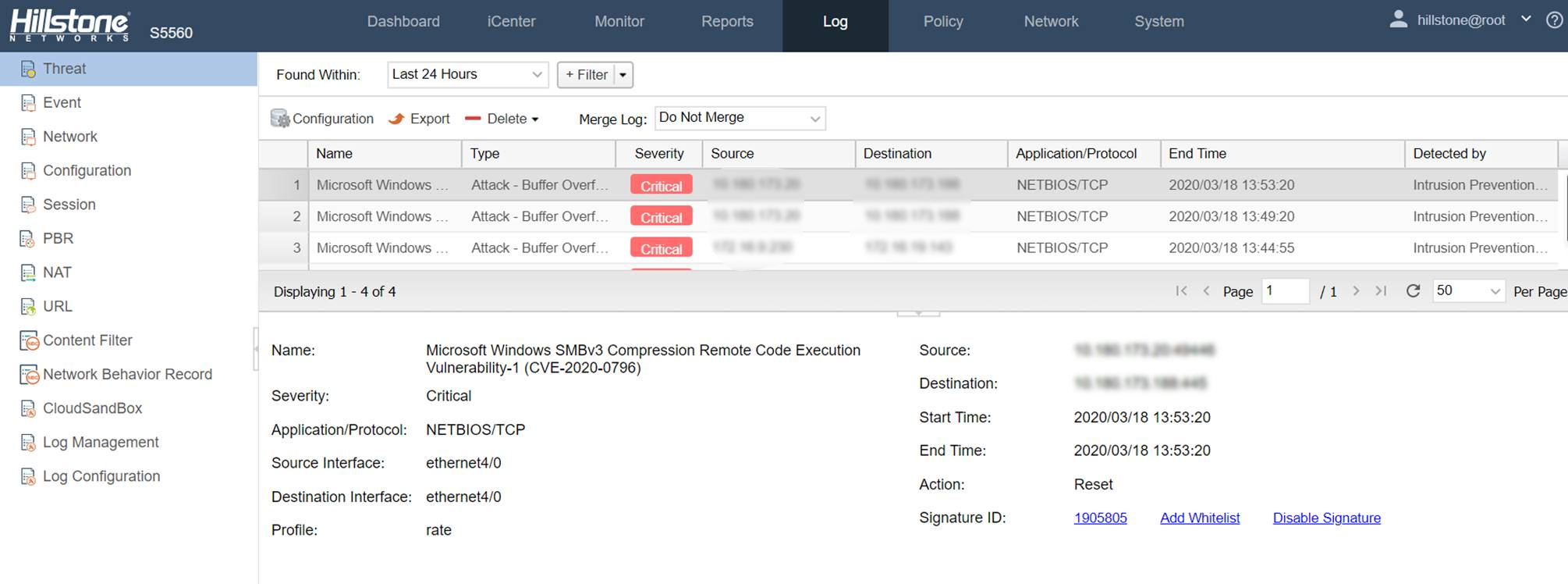
Threat Events Detected by Hillstone Solutions
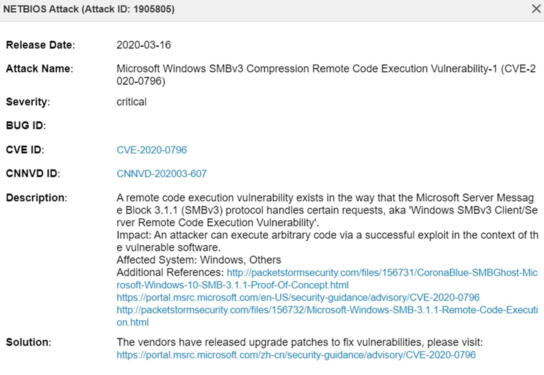
Vulnerability Detail Description



